Algebraic immunity of Boolean functions
Algebraic immunity of Boolean functions
In 2003, the discovery of algebraic immunity and annihilators have significantly impacted cryptanalysis by shaping how cryptographers approach the design of secure Boolean functions used in stream ciphers. These concepts have now become integral in defending against algebraic attacks. In fact, to achieve optimum resistance against those, cryptographers had to generally increase the number of variables in their constructions and choose functions with as high algebraic immunity as possible.
Among impacted designs was the filter generator, a technique used to break linearity in most LFSR-based stream ciphers by simply filtering the output of an LFSR through a highly non-linear boolean function. The concept of algebraic immunity shook it to its core as it appears a function with all previously required properties (nonlinearity, balancedness and resistance to fast algebraic attacks) in addition to great algebraic immunity was nowhere to be found until 2008 where an infinite class of such function possessing all mandatory features has been discovered[1].
Algebraic immunity and annihilators
The algebraic immunity of a function measures its resistance to algebraic attacks. Specifically it refers to the minimum algebraic degree of a non-zero Boolean function (called the annihilator of ) that annihilates or its complement.
Formally, let Failed to parse (Conversion error. Server ("https://wikimedia.org/api/rest_") reported: "Cannot get mml. Server problem."): {\displaystyle f:\mathbb {F} _{2}^{n}\rightarrow \mathbb {F} _{2}} be a Boolean function. An annihilator of or is a non-zero Boolean function such that .
The algebraic immunity of a boolean function is defined as the minimum algebraic degree among its annihilators .
For all Boolean functions, the algebraic immunity is bounded by .
Example through code
Boolean functions are defined within Sagemath[2] by importing the sage.crypto.boolean_function module and its components which are not loaded by default. With Sagemath a Boolean function can be created from its truth table or from a Boolean polynomial. The example below illustrates the latter.
sage: from sage.crypto.boolean_function import BooleanFunction
sage: B.<x0, x1, x2, x3> = BooleanPolynomialRing(4)
sage: f = x0*x1*x2*x3 + x0*x2*x3 + x1*x2*x3 + x0*x1 + x0*x3 + x1*x2 + x3 + 1
sage: F = BooleanFunction(f)
sage: F.algebraic_degree()
4
It is possible to compute an annihilator of F which algebraic degree is equal to . Note that but and has optimal algebraic immunity in this example.
sage: AI, g = F.algebraic_immunity(annihilator=True)
sage: AI
2
sage: g
x0*x3 + x3
sage: f * g == 0
True
Characterization of annihilators by the Walsh transform
If is an annihilator of , then and must be orthogonal functions over . This orthogonality property can be visualized through the Walsh coefficients of both functions.
Recall that for any two Boolean functions and , the integer addition is defined as . However so this reduces to Failed to parse (Conversion error. Server ("https://wikimedia.org/api/rest_") reported: "Cannot get mml. Server problem."): {\displaystyle f+g=f\oplus g} or the classical field addition. This reduction through annihilators directly leads to the following formula
that generalizes for all as
with .
Example through code
Recalling previously defined variables, the walsh coefficients can be directly computed as a list.
sage: _, g = F.algebraic_immunity(annihilator=True)
sage: G = BooleanFunction(g)
sage: F_plus_G = BooleanFunction(f + g)
sage: wf = F.walsh_hadamard_transform()
sage: wg = G.walsh_hadamard_transform()
sage: wfg = F_plus_G.walsh_hadamard_transform()
And verify that the equation holds.
sage: n = F.nvariables()
sage: for a in range(1, 2^n):
....: assert wfg[a] == wf[a] + wg[a]
Perfect algebraic immune functions
A perfect algebraic immune function[3] is a Boolean function such that for any pair of strictly positive integers where Failed to parse (Conversion error. Server ("https://wikimedia.org/api/rest_") reported: "Cannot get mml. Server problem."): {\displaystyle e+d<n} and , there is no Boolean function that satisfies and .
The conditions on are designed to restrict the potential space of attack functions making it more difficult to reduce the complexity of the function using algebraic methods. This criteria makes perfect algebraic immunity a highly desirable property in the construction of stream ciphers.
Balanced perfect algebraic immune functions[4][3] can exist only if is equal to 1 plus a power of 2. Unbalanced perfect algebraic immune functions exist only if is a power of 2.
Consequences of algebraic attacks on the design of stream ciphers
A difference by 1 in the algebraic immunity of a function Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} , used as combiner or filter in a stream cipher, makes a big difference in the efficiency of algebraic attacks. The designer needs then to choose Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} with optimal or near-optimal algebraic immunity. Ideally, one would choose a perfectly algebraic immune function, but finding such functions that also satisfy other key properties, like nonlinearity or balancedness, is not straightforward.
Let Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} be an Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle n} -variable Boolean function with algebraic immunity Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \lceil\frac{n}{2}\rceil} used to filter an LFSR of length Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle N \geq 2k} where Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle k} is the length of the key. The time complexity of an attack using an annihilator of degree Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \lceil\frac{n}{2}\rceil} , where realistic parameters involve Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle N = 256} and Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle k = 128} , would be roughly Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle 2^{80}} [5].
However, if the attacker knows several linearly independent annihilators with said degree, then the number of variables must be increased to approximately 20 in practice. This impacts the computational efficiency of stream ciphers that used to deal with at most 10 variables Boolean functions before.
Combining high algebraic immunity with high nonlinearity
Boolean functions for building stream ciphers are chosen to allow resistance to all known attacks and possibly to be computable as fast as possible. In that sense, finding a function achieving optimal or almost-optimal algebraic immunity and high nonlinearity remains a challenge.
Many studies[6][7][8][9][10][11] had been carried out to seek for the best functions class that would ensure both properties but eventually led to one of the parameters being too low for cryptographic purposes. Hence the need for design in an infinite class of functions achieving all the necessary criteria remained open until a work from Carlet and Feng[1] in 2008.
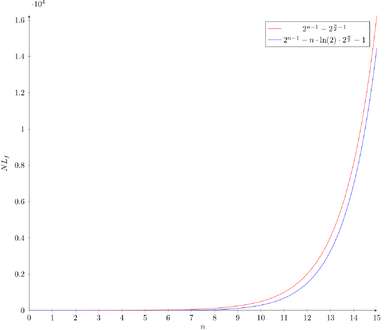
The primary construction of this class defines functions over Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \mathbb{F}_{2^n}} . For any integer Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle s} and any primitive element Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \alpha} of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \mathbb{F}_{2^n}} , all balanced Boolean functions whose support is Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \{\alpha^s, \ldots, \alpha^{2^{n-1} + s - 1}\}} have optimal algebraic Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \lceil\frac{n}{2}\rceil} . Their nonlinearity is also suitable for cryptographic purposes and a lower bound[12] is Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \mathcal{NL}_f \geq 2^{n-1} - n \cdot \ln{2} \cdot 2^{n/2} - 1} that is asymptotically similar to the covering radius bound.
While this bound is insufficient to prove strong general resistance for Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} , the nonlinearity has been exhaustively computed up to Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle n = 26} and the results happen to be highly favorable and sufficient. The good resistance to fast algebraic attacks has also been proved[3] for all Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle n} . Hence these functions gather all the properties needed to build filters in stream ciphers resistant to all the main attacks.
Applications of algebraic immunity to cryptanalysis
A new kind of attacks, called algebraic attacks, was introduced in 2003 by Courtois and Meier[5] and has significantly changed the situation with Boolean functions in stream ciphers. These attacks aim to directly recover the key or the internal state of the system by solving a system of multivariate equations and are as efficient as Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle AI(f)} is small.
Algebraic attacks: using the annihilator to reduce the degree
Suppose the output Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle s_i} of a stream cipher (or its internal state) depends on some nonlinear function Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} of high algebraic degree with Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle n} variables. Expressing each output bit in terms of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} offers a system of multivariate equations of high degree. There exists methods to solve such a system using Gröbner bases[13] but the high algebraic degree of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} makes this attack impractical and computationally too expensive for real-life scenarios.
However, it is possible to lower the cost of solving such a system by considering annihilators of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} . Consider the first scenario and assume the existence of two functions Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} and Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle h} such that Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle fg = h} both of low algebraic degree and Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g, h \neq 0} . Then each output Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f(x) = s_i} can be expressed as Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle fg = gs_i = h} regarding
However, if Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} has high algebraic degree but Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle h} has low algebraic degree, we must consider the scenario above with one additional constraint on the choice of the equations;
If Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} has high algebraic degree then so will Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g - h} thus this equation is discarded when Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle s_i = 1} .
In the third scenario, if Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} is an annihilator of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} , then Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle fg = 0} and if
For the latter, if Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} is a non-zero function of low degree Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle d} , then the equation Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g = 0} will carry the same degree Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle d} for each output Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle s_i = } meaning that given Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle m} keystream bits, an average of Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle m/2} multivariate equations of degree Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle d} can be derived.
Gröbner bases
When as many as the required Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle O(\binom{n}{d})} keystream bits are not available, the system of multivariate equations can be solved with Gröbner bases algorithms but at a consequential increased cost in computations.
Linearization
In practice if Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle h} and Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle g} have sufficiently low algebraic degree (i.e. if Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle f} has poor algebraic immunity), it is possible to linearize the system by considering each monomial as a unique variable. However, the number of variables grows exponentially in the algebraic degree of the annihilator and is equal to Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle D = \textstyle \sum_{i = 0}^{d^\circ(g)} \binom{n}{i}} and solving a system of linear equations via Gaussian elimination takes Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle O(D^\omega)} operations where Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \omega \approx 3} is the exponent of the Gaussian reduction.
References
- ↑ 1.0 1.1 C. Carlet and F. Keng. An infinite class of balanced functions with optimum algebraic immunity, good immunity to fast algebraic attacks and good nonlinearity. Proceedings of ASIACRYPT 2008, Lecture Notes in Computer Science 5350 pp. 425-440, 2008.
- ↑ SageMath, the Sage Mathematics Software System (Version 10.4), The Sage Developers, 2024, https://www.sagemath.org.
- ↑ 3.0 3.1 3.2 M. Liu, D. Lin, and D. Pei. Perfect algebraic immune functions. Proceedings of ASIACRYPT 2012, Lecture Notes in Computer Science 7658, pp. 172-189, 2012.
- ↑ Y. Du and F. Zhang. On the existence of Boolean functions with optimal resistance against fast algebraic attacks. IACR Cryptology ePrint Archive (http://eprint.iacr.org/) 2012/210, 2012.
- ↑ 5.0 5.1 N. Courtois and W. Meier. Algebraic Attacks on Stream Ciphers with Linear Feedback; Extended Version of the Eurocrypt 2003 paper, August 24, 2003. Proceedings of CRYPTO 2003, Lecture Notes in Computer Science 2501, pp. 346-359.
- ↑ A. Braeken and B. Preneel. On the algebraic immunity of symmetric Boolean functions. Proceedings of Indocrypt 2005, Lecture Notes in Computer Science 3797 pp.35-48, 2005. Some false results in this reference are corrected in Braeken's PhD thesis "Cryptographic properties of Boolean functions and S-boxes.".
- ↑ C. Carlet, D. Dalai, K. Gupta, and S. Maitra. Algebraic immunity for cryptographically significant Boolean functions: analysis and construction. IEEE Transactions on Information Theory 52 (7), pp. 3105-3121, 2006.
- ↑ D. K. Dalai, K. C. Gupta, and S. Maitra. Results on algebraic immunity for cryptographically significant Boolean functions. Proceedings of Indocrypt 2004, Lecture Notes in Computer Science 3348, pp. 92-106, 2004.
- ↑ D. K. Dalai, K. C. Gupta, and S. Maitra. Cryptographically significant Boolean functions: construction and analysis in terms of algebraic immunity. Proceedings of Fast Software Encryption FSE 2005, Lecture Notes in Computer Science 3557, pp. 98-111, 2005.
- ↑ D. K. Dalai, S. Maitra, and S. Sarkar. Basic theory in construction of Boolean functions with maximum possible annihilator immunity. Designs, Codes and Cryptography 40 (1), pp. 41-58, 2006 (preliminary version available in IACR Cryptology ePrint Archive http://eprint.iacr.org/2005/229, 2005)
- ↑ E. Pasalic. Almost fully optimized infinite classes of Boolean functions resistant to (fast) algebraic cryptanalysis. Proceedings of ICISC 2008, Lecture Notes in Computer Science 5461, pp. 399-414, 2008.
- ↑ N. Brandstätter, T. Lange, and A. Winterhof. On the non-linearity and sparsity of Boolean functions related to the discrete logarithm infinite fields of characteristic two. Proceedings of International Workshop on Coding and Cryptography WCC 2005, Lecture Notes in Computer Science 3969, pp. 135-143, 2006.
- ↑ G. Ars and J.-C. Faugère. An Algebraic Cryptanalysis of Nonlinear Filter Generators using Gröbner bases. Rapport de Recherche INRIA 4739, 2003.